Video Doorbell Advice and Settings for Opting Out of the Surveillance State

There’s also the risk that footage falls into the wrong hands and ends up enabling politically-motivated investigations, police harassment, or stalking without you intending or even knowing about it. Maybe company employees or third-party contractors gain access to videos, or your cameras are hacked. Amazon settled a privacy lawsuit brought by the FTC that mentioned […]
How to Prepare for Tomorrow’s Wars by James Ryseff

en English Politics Feb 25, 2026 James Ryseff Just as established corporations facing challenges from innovative startups must adapt or die, militaries must continually renew themselves to remain effective against emerging threats. For democracies today, this means investing in evolving technologies and embracing new ways of operating. WASHINGTON, DC – We are living through a […]
How to Organize Safely in the Age of Surveillance

For all these approaches, from the fully public to the paranoid, the same principle applies as in a Signal conversation: A piece of information is only as secure as the least secured device that accesses it. So as you consider your threat model and whose devices and accounts within your group have access to your […]
How to Protect Your iPhone or Android Device From Spyware

Infection usually starts through malicious links and fake apps, but it is also taking place via “more subtle methods,” says Richard LaTulip, a field CISO at security company Recorded Future, which collaborated with Google’s threat intelligence team on the Predator spyware findings. LaTulip cites the example of recent research on malicious browser extensions affecting millions […]
How to Set Up a Google Home Security System: Best Cameras, Doorbells, and Other Devices
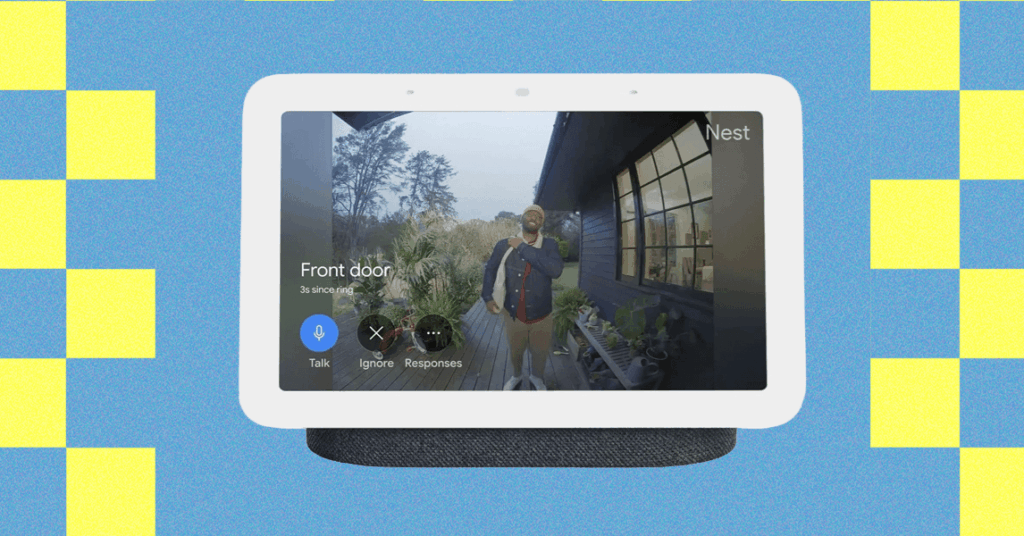
There’s no need for an expensive, professionally installed home security system for a little peace of mind. You can keep tabs on your home when you’re away, check in on your kids or pets, and discourage intruders with a few well-placed security cameras and connected devices. Easily the smartest option on the market right now, […]
How to Use Passkeys With Google Password Manager (2025)
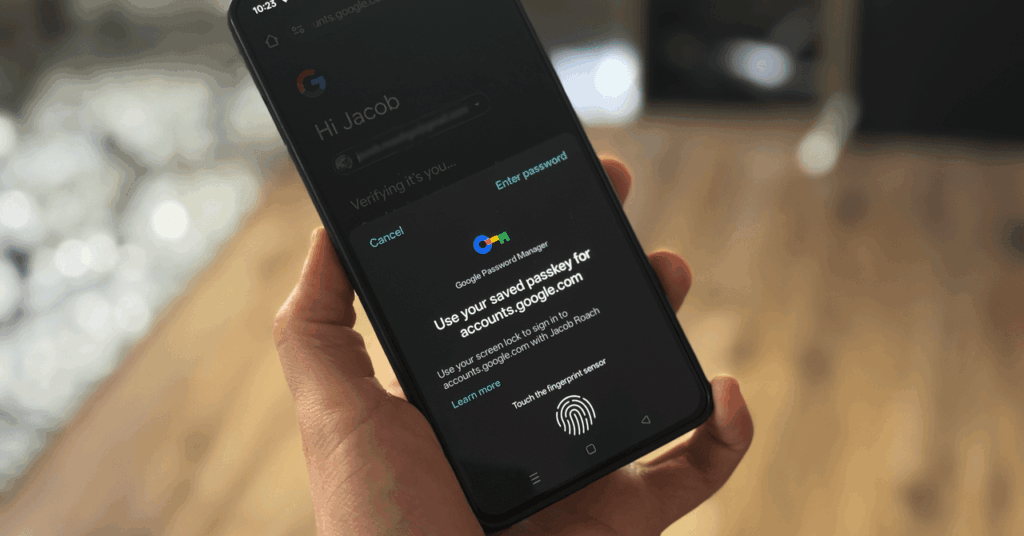
Google wants you to start using passkeys. Its vision is to “progress toward a passwordless future,” allowing you to store passkeys in the Google Password Manager service. For websites that support the login method, Google now allows you to generate, store, and sync passkeys. The problem is actually finding a consistent way to do it. […]
How to Use a Password Manager to Share Your Logins After You Die (2025)
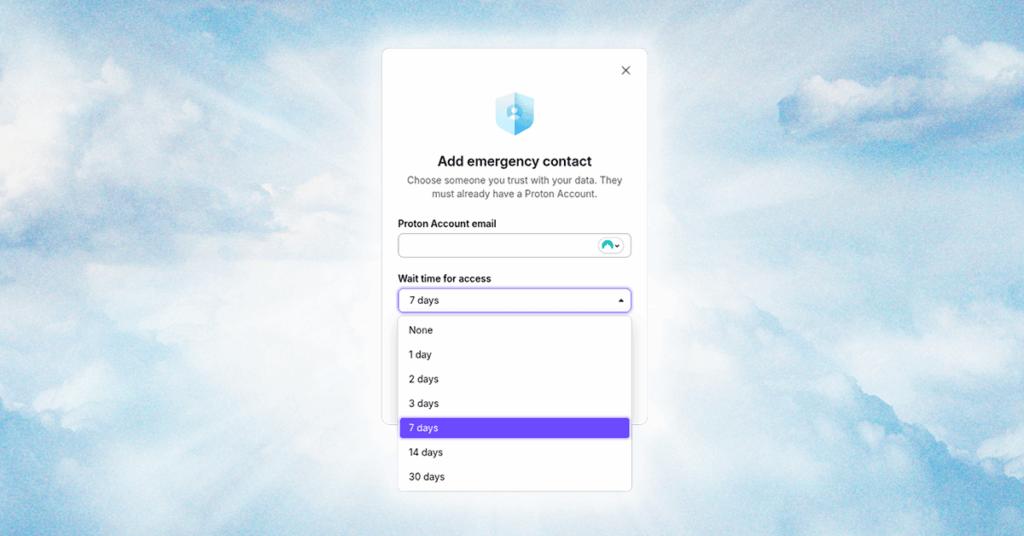
It’s not fun to talk about, but there’s only one thing certain in life. You need to have a plan for your digital legacy, just like you make a plan for your physical assets; otherwise, your accounts, services, and logins will rot away in a data center before they’re inevitably erased by a data retention […]
How to Use 1Password’s Travel Mode at the Border (2025)
Enter VeraCrypt. It’s a free, open source encryption app that can encrypt full drives, as well as operating system partitions, similar to BitLocker or FileVault. The big feature of VeraCrypt is plausible deniability. There are specific setup steps, but you can store an encrypted partition within an encrypted partition. When you encrypt a drive with […]
How to Set Up and Use a Burner Phone

When you are done with the burner phone, make sure that you get rid of it in a thoughtful way as well. “At the end of the intended use, consider steps to eliminate information, remove SIM cards and/or memory cards, making sure not to leave a potential vulnerability after you,” says Access Now’s Al-Maskati. Using […]
How to set up Single Sign-On in AWS (IAM Identity Center)
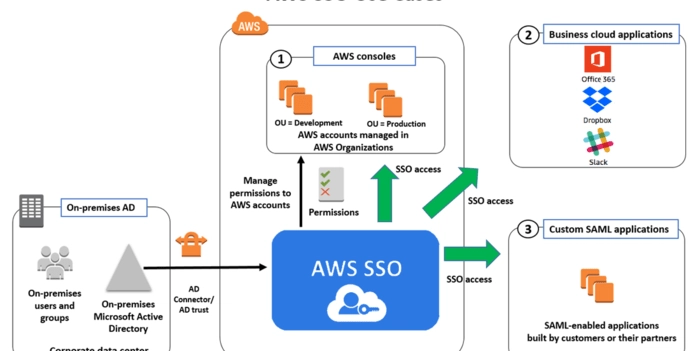
When I was at university, I met some programmers who were finishing their software engineering degrees. Some of them were already working, and they gave me what is still one of the best pieces of advice I’ve ever received about this craft: “If you want to be good, stick with university knowledge. If you want […]